
CHM |

|

|

|

|
||
CHM |

|

|

|

|

|
To secure a CHM file (help file) the Windows viewer for this file - hh.exe is used. By default, every Windows system should have this file installed.
There are 3 steps to protect the CHM file:
Copy the viewer for the chm file, the file hh.exe from c:\windows to your project folder where you saved the CHM file.
![]() The hh.exe from a Vista machine will not run on XP but the version from XP will run on Vista machines. If you want to support NT you have to make tests which hh.exe will run on all operating systems.
The hh.exe from a Vista machine will not run on XP but the version from XP will run on Vista machines. If you want to support NT you have to make tests which hh.exe will run on all operating systems.
![]() It is not in the liability of Mirage if you may distribute this file or not.
It is not in the liability of Mirage if you may distribute this file or not.
To run with Multimedia Protector, a special start application is needed. Copy the file startchm.exe and the configuration file chm.ini from the Multimedia Protector installation folder ...\tools\chm to your project folder where you saved the CHM file.
Now add the name of your chmfile in the chm.ini file. You can use any text editor to modify this file.
[Filename]
chmfile=test.chm (change the name here)
The folder contains now all files which are:
•hh.exe
•startchm.exe and chm.ini
•your chm file
Now import all the files from the project folder you created and mark startchm.exe as startfile using the button Define as starting file. A red icon signals the start file.
The import screen would show the following files.
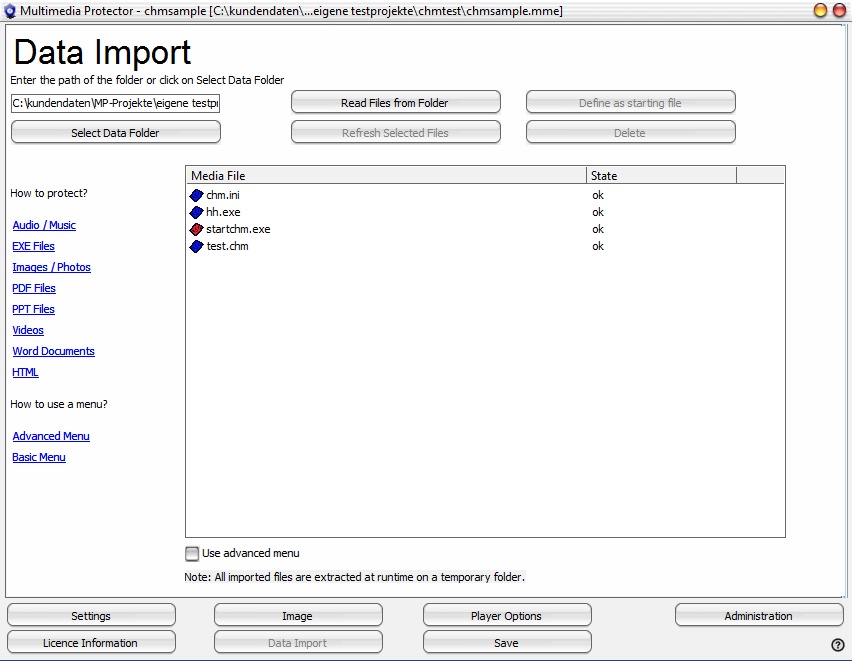
The following EXE options are mandatory for CHM protection
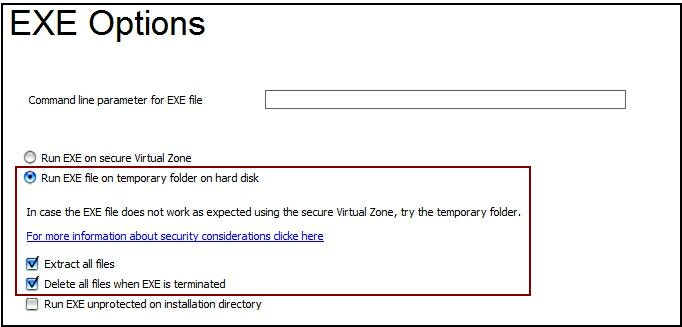
All all options of CHM files are supported but with the limitation of the EXE protection.
MIRAGE MAKES NO REPRESENTATION, WARRANTY, OR GUARANTY AS TO THE RELIABILITY, TIMELINESS, QUALITY, SUITABILITY, TRUTH, AVAILABILITY, ACCURACY OR COMPLETENESS OF THE SOFTWARE MENTIONED IN THIS TUTORIAL. MIRAGE DOES NOT REPRESENT OR WARRANT THAT (A) THE USE OF THE SOFTWARE WILL BE SECURE, TIMELY, UNINTERRUPTED OR ERROR-FREE OR OPERATE IN COMBINATION WITH ANY OTHER HARDWARE, SOFTWARE, SYSTEM OR DATA, (B) THE SOFTWARE WILL MEET YOUR REQUIREMENTS OR EXPECTATIONS, (C) ERRORS OR DEFECTS WILL BE CORRECTED, OR (D) THE SOFTWARE IS FREE OF VIRUSES OR OTHER HARMFUL COMPONENTS. YOU ARE RESPONSIBLE TO ENSURE THAT THE SOFTWARE IS USED WITHIN THE LIMIT OF THE LICENSE AGREEMENT OF THE SOFTWARE.
|